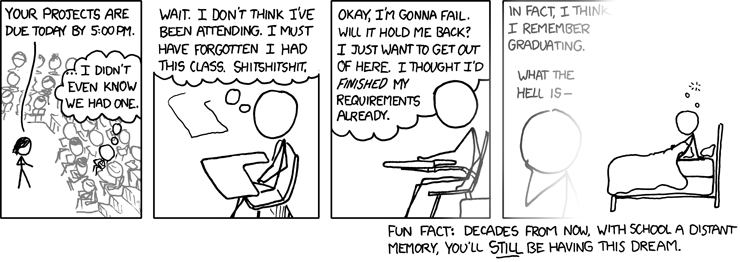
Thursday, September 09, 2010
Happened again...
Frigging Uni-related PTSD... It's been more than a decade now, please, when will I stop having these?
Sunday, September 05, 2010
OpenVPN behind a firewall with SSH
Serverside config
##############################
# Install Bridging
sudo apt-get install bridge-utils
##############################
# Modify /etc/network/interfaces
vi /etc/network/interfaces
==========================
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
#auto eth0
#iface eth0 inet dhcp
auto br0
iface br0 inet static
address 192.168.1.64
#network 192.168.
netmask 255.255.255.0
gateway 192.168.1.254
bridge_ports eth0
bridge_fd 9
bridge_hello 2
bridge_maxage 12
bridge_stp off
#Bridge setup
#auto br0
#iface br0 inet static
#address 192.168.1.61
#netmask 255.255.255.0
#gateway 192.168.1.254
#bridge_ports eth0
==========================
# Install OpenVPN
apt-get install openvpn
##############################
#Generate some keys:
mkdir /etc/openvpn/easy-rsa
cp -r /usr/share/doc/openvpn/
chown -R root /etc/openvpn/easy-rsa
vi /etc/openvpn/easyrsa-vars # and edit the following
==========================
export KEY_COUNTRY="Zoo"
export KEY_PROVINCE="Apes"
export KEY_CITY="Monkey Cage"
export KEY_ORG="Baboons"
export KEY_EMAIL="bob@thebaboon.zoo"
==========================
cd /etc/openvpn/easy-rsa/
source vars
./clean-all
./build-dh
./pkitool --initca
./pkitool --server server
cd keys
openvpn --genkey --secret ta.key
sudo cp server.crt server.key ca.crt dh1024.pem ta.key /etc/openvpn/
##############################
#Create the client keys:
cd /etc/openvpn/easy-rsa
. vars
./pkitool photon
scp /etc/openvpn/ca.crt hakan@photon:~/openvpn
scp /etc/openvpn/easy-rsa/keys/
scp /etc/openvpn/easy-rsa/keys/
scp /etc/openvpn/ta.key hakan@photon:~/openvpn
##############################
#Configure the server:
sudo cp /usr/share/doc/openvpn/
sudo gzip -d /etc/openvpn/server.conf.gz
vi /etc/openvpn/server.conf and modify
==========================
local 192.168.1.64
dev tap0
up "/etc/openvpn/up.sh br0"
down "/etc/openvpn/down.sh br0"
;server 10.8.0.0 255.255.255.0
server-bridge 192.168.1.66 255.255.255.0 192.168.1.220 192.168.1.239
push "route 192.168.1.254 255.255.255.0"
push "dhcp-option DNS 192.168.1.254"
push "dhcp-option DOMAIN lan"
cipher AES-256-CBC
keepalive 3 200
tls-auth ta.key 0 # This file is secret
user nobody
group nogroup
==========================
vi /etc/openvpn/up.sh
==========================
#!/bin/sh
BR=$1
DEV=$2
MTU=$3
/sbin/ifconfig $DEV mtu $MTU promisc up
/usr/sbin/brctl addif $BR $DEV
==========================
vi /etc/openvpn/down.sh
==========================
#!/bin/sh
BR=$1
DEV=$2
/usr/sbin/brctl delif $BR $DEV
/sbin/ifconfig $DEV down
==========================
sudo apt-get install openvpn
Then with the server configured and the client certificates copied to the /etc/openvpn/ directory, create a client configuration file by copying the example. In a terminal on the client machine enter:
sudo cp /usr/share/doc/openvpn/
dev tap
sudo update-rc.d -f openvpn remove
##############################
# Install Bridging
sudo apt-get install bridge-utils
##############################
# Modify /etc/network/interfaces
vi /etc/network/interfaces
==========================
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
#auto eth0
#iface eth0 inet dhcp
auto br0
iface br0 inet static
address 192.168.1.64
#network 192.168.
netmask 255.255.255.0
gateway 192.168.1.254
bridge_ports eth0
bridge_fd 9
bridge_hello 2
bridge_maxage 12
bridge_stp off
#Bridge setup
#auto br0
#iface br0 inet static
#address 192.168.1.61
#netmask 255.255.255.0
#gateway 192.168.1.254
#bridge_ports eth0
==========================
# Install OpenVPN
apt-get install openvpn
##############################
#Generate some keys:
mkdir /etc/openvpn/easy-rsa
cp -r /usr/share/doc/openvpn/
chown -R root /etc/openvpn/easy-rsa
vi /etc/openvpn/easyrsa-vars # and edit the following
==========================
export KEY_COUNTRY="Zoo"
export KEY_PROVINCE="Apes"
export KEY_CITY="Monkey Cage"
export KEY_ORG="Baboons"
export KEY_EMAIL="bob@thebaboon.zoo"
==========================
cd /etc/openvpn/easy-rsa/
source vars
./clean-all
./build-dh
./pkitool --initca
./pkitool --server server
cd keys
openvpn --genkey --secret ta.key
sudo cp server.crt server.key ca.crt dh1024.pem ta.key /etc/openvpn/
##############################
#Create the client keys:
cd /etc/openvpn/easy-rsa
. vars
./pkitool photon
scp /etc/openvpn/ca.crt hakan@photon:~/openvpn
scp /etc/openvpn/easy-rsa/keys/
scp /etc/openvpn/easy-rsa/keys/
scp /etc/openvpn/ta.key hakan@photon:~/openvpn
##############################
#Configure the server:
sudo cp /usr/share/doc/openvpn/
sudo gzip -d /etc/openvpn/server.conf.gz
vi /etc/openvpn/server.conf and modify
==========================
local 192.168.1.64
dev tap0
up "/etc/openvpn/up.sh br0"
down "/etc/openvpn/down.sh br0"
;server 10.8.0.0 255.255.255.0
server-bridge 192.168.1.66 255.255.255.0 192.168.1.220 192.168.1.239
push "route 192.168.1.254 255.255.255.0"
push "dhcp-option DNS 192.168.1.254"
push "dhcp-option DOMAIN lan"
cipher AES-256-CBC
keepalive 3 200
tls-auth ta.key 0 # This file is secret
user nobody
group nogroup
==========================
vi /etc/openvpn/up.sh
==========================
#!/bin/sh
BR=$1
DEV=$2
MTU=$3
/sbin/ifconfig $DEV mtu $MTU promisc up
/usr/sbin/brctl addif $BR $DEV
==========================
vi /etc/openvpn/down.sh
==========================
#!/bin/sh
BR=$1
DEV=$2
/usr/sbin/brctl delif $BR $DEV
/sbin/ifconfig $DEV down
==========================
Clientside config
sudo apt-get install openvpn
Then with the server configured and the client certificates copied to the /etc/openvpn/ directory, create a client configuration file by copying the example. In a terminal on the client machine enter:
sudo cp /usr/share/doc/openvpn/
Edit and modify the following
dev tap
proto tcp
remote monkeycage.zoo.com 1194 #(<-- replace this with localhost if you want to use SSH tunnelling)
cert photon.crt
key photon.key
tls-auth ta.key 1
cipher AES-256-CBC
remote monkeycage.zoo.com 1194 #(<-- replace this with localhost if you want to use SSH tunnelling)
cert photon.crt
key photon.key
tls-auth ta.key 1
cipher AES-256-CBC
sudo update-rc.d -f openvpn remove
##############################
# With SSH
# With SSH
ssh -fX -L1194:192.168.1.64:1194 monkeycage.zoo.com sleep 30
sudo /etc/init.d/openvpn start
sudo /etc/init.d/openvpn start
FreeNX on Ubuntu & CentOS
Fairly simple stuff.
When prompted about the key while running nxsetup, you should select Y and install your own key all around unless you want an unsecure connection.
Ubuntu:
CentOS:
You need the Extra Repos or the RPMS for expect libnxcl nx qt4 freenx
Expect & QT4 are in the normal distribution and should be already installed in most cases. Latest FreeNX and libnxcl from the Extra repos are:
Windows
download client from http://www.nomachine.com/download-client-windows.php
Apparently the nomachine client has problems with the DISPLAY_BASE.
If you connect to Server A and then Server B, it fails to open a port. Suprisingly, this works perfectly fine on qtnx client without any changes. For servers being accessed with Windows, edit /etc/freenx-server/node.conf and modify DISPLAY_BASE to have a unique value plus an offset for possible multiple connections
When prompted about the key while running nxsetup, you should select Y and install your own key all around unless you want an unsecure connection.
Ubuntu:
- sudo add-apt-repository ppa:freenx-team
- sudo apt-get update
- sudo aptitude install freenx qtnx
- wget https://bugs.launchpad.net/freenx-server/+bug/576359/+attachment/1378450/+files/nxsetup.tar.gz
- tar -zxf nxsetup.tar.gz && sudo mv nxsetup /usr/lib/nx/nxsetup && sudo chown root:root /usr/lib/nx/nxsetup && sudo /usr/lib/nx/nxsetup --install
- cd /etc/nxserver
- cp node.conf.sample node.conf (if necessary, see below)
CentOS:
You need the Extra Repos or the RPMS for expect libnxcl nx qt4 freenx
Expect & QT4 are in the normal distribution and should be already installed in most cases. Latest FreeNX and libnxcl from the Extra repos are:
- freenx-0.7.3-5.el5.centos.x86_64.rpm
- nx-3.4.0-3.el5.centos.x86_64.rpm
- libnxcl-0.9.0-3.el5.centos.x86_64.rpm
- yum install qtnx freenx
- nxsetup --install
- cd /etc/nxserver
- cp node.conf.sample node.conf (if necessary, see below)
Windows
download client from http://www.nomachine.com/download-client-windows.php
Apparently the nomachine client has problems with the DISPLAY_BASE.
If you connect to Server A and then Server B, it fails to open a port. Suprisingly, this works perfectly fine on qtnx client without any changes. For servers being accessed with Windows, edit /etc/freenx-server/node.conf and modify DISPLAY_BASE to have a unique value plus an offset for possible multiple connections
Subscribe to:
Posts (Atom)